Imagine sending a locked box through the mail, knowing that only you and the recipient hold the one key to open it. In the digital world, 256-bit encryption plays that same role, transforming your messages, files, and transactions into a virtual vault that’s practically unbreakable.
Whether you’re banking online, securing a private chat, or storing personal photos in the cloud, understanding how 256-bit keys work can give you peace of mind.
Contents

It starts from the security level and security claim, which are expressed in binary form. There is a private key with a value, and attackers must perform n number of operations to get these values.
This value is represented in the form of two types of numbers, containing ones (1’s) and zeros (0’s), in binary form. If there is a 2-bit key, then it needs to have 2² = 4 values.
What is Encryption?
In short, Encryption is the process of scrambling readable data (called plaintext) into an unreadable, garbled format (called ciphertext). To unscramble the ciphertext back into readable plaintext, you need a special key.
The process of converting one normal format of data into an unauthorized format to increase data security. The encryption and Decryption method is used to process that data and prevent any cyber attack. There are different keys used to encrypt data in a normal format. Here, it is used as a 256-bit Encryption.
Before we discuss this 256-bit Encryption, let’s learn some things about Encryption. When we use data to perform an algorithmic function, this type of data is referred to as plain text, which means unencrypted data. After completing the function, it creates an encrypted ciphertext.
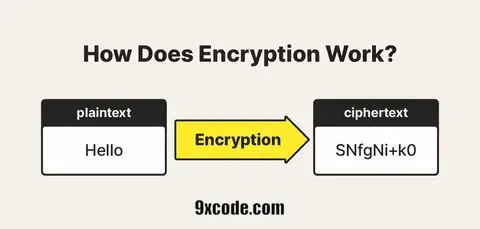
Practical Example
- Plaintext: Your original message (e.g., “
Hello, I love 9xcode.com“). - Encryption Algorithm: Algorithm used to encrypt message (e.g.,
AES 256) - Ciphertext: The scrambled output (e.g., “
iG1RaW0x8qKB0Y4nb+VefmuhIyNrMG0x“). - Decryption: Reversing the process using the correct key to get the original message.
The algorithms are referred to as keys and can be utilized in two primary ways. First, public keys are used in asymmetric encryption to keep secrets, and second, private keys are used for practical means of decryption.
There is a flow for encryption and decryption in which, firstly, it is all available in plaintext form. It’s encrypted to ciphertext and then decrypted again to the plaintext form. Plaintext form is a readable form of messages.
What Does 256-Bit Encryption Mean?
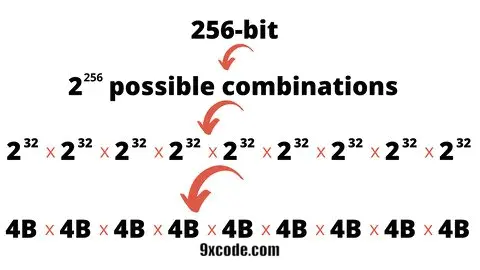
Now we get to the main event. 256-bit encryption means the key used to encrypt and decrypt your data is 256 bits long. Several possible cases in the form of 2256 are 2 x 2, x 2, x 2… 256 times.
This means there are 2256 possible key combinations.
Now, just look at how massive that number is.
2256 is roughly 1.15 x 10⁷⁷ (1.157920892×10⁷⁷)
That’s a number with 78 digits. It looks like this:
115,792,089,237,316,195,423,570,985,008,687,907,853,269,984,665,640,564,039,457,584,007,913,129,639,936.
The inner side of the algorithm uses a key-based number of combinations to convert data into an encrypted format. For 256-bit encryption, 2256 different combinations are created, from which one should be selected as per the algorithm. This process makes the data secure on another level.
How Secure Is 256-Bit Encryption from Hackers?

The most common way hackers try to break encryption is with a brute-force attack. They use a computer to try every single possible key combination, one by one, until they find the right one.
To brute-force crack it, a hacker would need to guess the correct key from:
115,792,089,237,316,195,423,570,985,008,687,907,853,269,984,665,640,564,039,457,584,007,913,129,639,936 options. Even the world’s fastest supercomputer would take billions of years to succeed. That’s why it’s called “unbreakable” and is used by governments, militaries, and major financial institutions.
A decryption key is required to convert data from an encrypted form (ciphertext) to a normal form (plaintext). If the attacker somehow gets the decryption key, they will be able to access all the data. You should prevent the decryption key from leaking. The decryption key is the only way to convert all your data from an encrypted form to a normal form.
This security is called public key cryptography, one of the strongest security methods. It can be solved by calculating the implementation’s computational complexity.
How Does AES 256-bit Encryption Work?
AES 256-bit Encryption stands for Advanced Encryption Standard with a 256-bit key. It’s used in everything from banking systems to military communications. It’s most secure and widely used symmetric encryption algorithms in the world. Let’s understand how AES 256-bit Encryption Works.
AES is a symmetric key algorithm, which means the same key is used for encryption and decryption. The 256-bit key is expanded into multiple round keys. AES 256-bit creates 15 round keys, from which 1 is the initial round key. An algorithm applied to those round keys includes substitutions and shifts on bytes using Rijndael’s Key Schedule.
Step-by-Step Process of Encryption
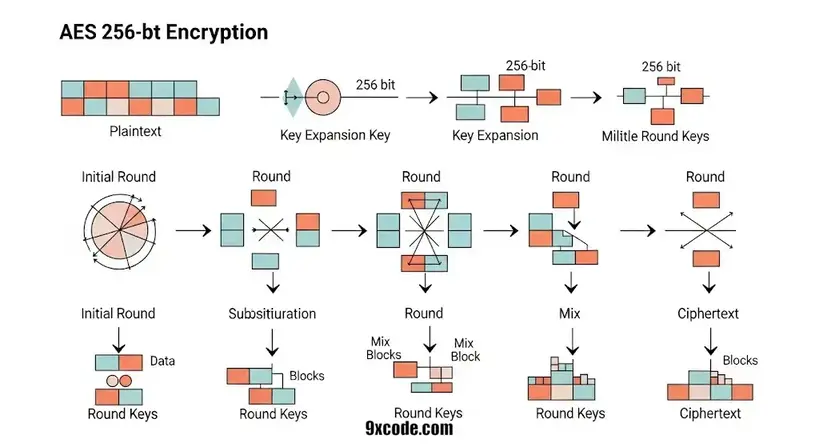
Initial Round
AddRoundKey: The 128-bit plaintext block is XORed with the first round key(initial round). Here, mixes the data with the key to begin scrambling the content to secure.
Main Rounds (Other 14 Rounds for AES 256-Bit)
- SubBytes: Each byte in a 16-byte block is replaced with another byte using a predefined Substitution box. It creates a non-linearity of pattern, which makes it hard to detect.
- ShiftRows: Rows of a 4*4 byte matrix are shifted to the left by different offsets. The second, Third, and Fourth rows are shifted by 1,2, and 3, respectively. After shifting, Diffusion is applied for spreading the byte across the block.
- MixColumns: Galois Field(2^8) Algorithms used to mix the data within each column to spread byte influence mathematically using matrix multiplication. It is used until 13 Round only, not applied on the 14th or Final Round.
- AddRoundKey: The block is XORed again with the current round key. Over here, the key is directly used in the current round.
Encrypted Output
The output is 128-bit encrypted data(ciphertext). For decrypting that data, the same key is required to reverse the process.
Comparing 128-Bit vs. 256-Bit Encryption
| Feature | AES-128 | AES-256 |
|---|---|---|
| Key Space | 2¹²⁸ combinations | 2²⁵⁶ combinations (2¹²⁸× larger) |
| Security | Extremely strong; safe for most purposes | Slightly slower, but modern hardware bridges the gap |
| Performance | Faster encryption/decryption | Slightly slower, but modern hardware bridges gap |
| Future-Proofing | Good against classical attacks; less margin for quantum threats | Better margin against emerging quantum attacks |
Common Types of 256-Bit Encryption
Asymmetric encryption is based on mathematical problems that are easy to encrypt. On the other hand, the process of decryption is the reverse process. It’s quite difficult to do.
Decryption is an attack against asymmetric public keys, which is why using symmetric encryption by using private keys on a brute force style search of the key space.
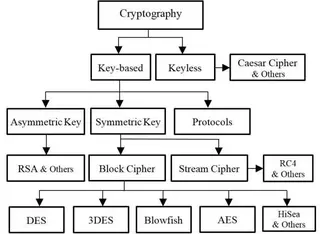
The most commonly used encryption algorithm includes RSA, AES, and ECC. AES is used to compare both symmetric and asymmetric encryption based on security and processing speed.
Symmetric Encryption is best for security purposes because it’s hard to break down by brute-force methods, but it is slower and less efficient to apply. For most places, AES-128 is preferred to work faster and provide efficiency in working. For more security, we prefer to choose AES-256 encryption.
Real-World Example: How TLS & AES-256 Protects Your Online Messages
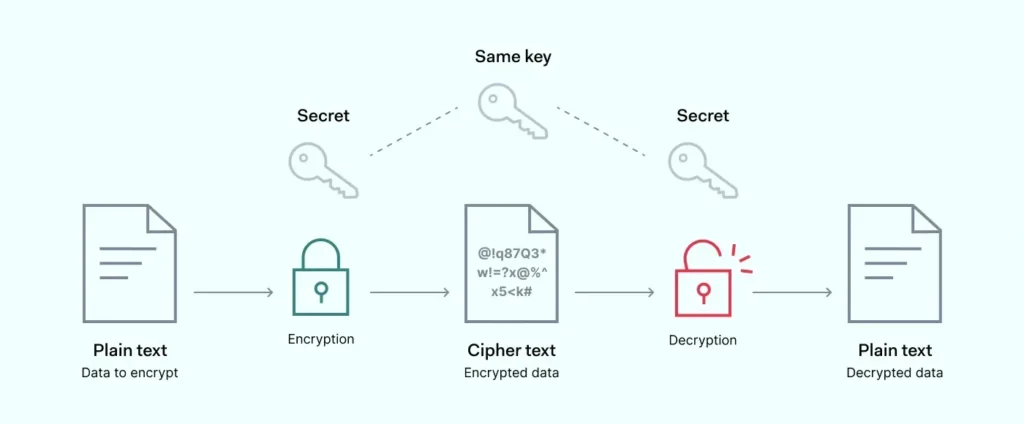
Let’s discuss an example of AES-256 security for encryption/decryption of messages over the internet for secure sharing of your private data.
While transferring data on the internet, there are encrypted data is sent or received. For receiving corrected and plaintext messages from the sender, there are decryption tools available on machines to convert encrypted data. For sending data securely, an encrypter is available in the sender’s machine to convert normal to ciphertext.
TLS (Transport Layer Security) and SSL (Secure Socket Layer) are used to send and receive messages from one place to another. For the security of messages from leaks via the internet, TLS and SSL protocols are used.
Key Management
To maintain security, you need to learn about the management of encryption keys. Who to share the key and how to protect it?
Generate a strong and randomized key such that no one can predict the data encryption key.
Remind that you have to change the key over time, the reason that if someone gets the key, they will not be able to use the data for a long time.
Share the key with people on your team and trustworthy people only. Also uses a key for a key, which makes it more secure.
Read Next: Complete VS Code Tutorial: Install, Features, Web Dev Setup, Requirements
Conclusion
256-bit Encryption provides high-level security using a key, making the data nearly impossible to crack. It’s fast, efficient, widely supported, and trusted by top companies, banks, military. You can use their algorithms to provide security for your crafted products. Encryption will solve your problem of remembering the password for years. Just remember the key and encrypt all your passwords through that key.
Thank you author, Great information and this only cover all the queries what i had in my mind.
thanks once again.